The Shared Responsibility Model: Demystifying Cloud Security
Cloud computing has revolutionized how businesses operate, offering unprecedented scalability and flexibility. However, it has also introduced a fundamental shift in cybersecurity. The old model, where an organization was solely responsible for securing its entire on-premise infrastructure, no longer applies. In the cloud, security is a Shared Responsibility. This model, adopted by major cloud providers like AWS, Azure, and Google Cloud, defines the specific obligations of both the provider and the customer.
Failing to grasp this distinction is a top cause of security incidents, as organizations mistakenly assume their cloud provider handles all security. To avoid this common pitfall, it’s essential to understand the two sides of the model: Security OF the Cloud and Security IN the Cloud.
Security OF the Cloud: The Provider’s Job 🔐
The cloud provider is responsible for securing the global infrastructure that powers the cloud services. Think of it as the secure foundation upon which you build your workloads. This includes:
-
- Physical Infrastructure: The data centers, servers, storage hardware, and networking equipment. This means physical access controls, fire suppression, and environmental systems are the provider’s responsibility.
-
- Virtualization: Ensuring the security of the hypervisor and the core services that allow for multi-tenancy and resource isolation.
-
- Managed Services: For higher-level services like Platform-as-a-Service (PaaS) or Software-as-a-Service (SaaS), the provider takes on more responsibility for the underlying components, such as the operating system, database patching, and network configurations.
The provider’s job is to ensure the cloud itself is protected and available.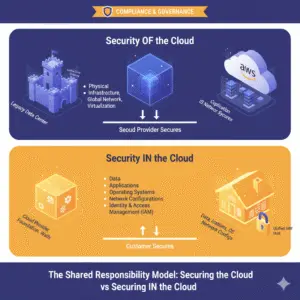
Security IN the Cloud: Your Job 🔒
This is the customer’s primary responsibility, and it’s where the vast majority of cloud breaches occur. You are accountable for the security of everything you place and manage within the cloud environment. Your responsibilities include:
-
- Data: This is the most crucial asset. You are responsible for protecting your data through encryption (at rest and in transit), access controls, and data loss prevention (DLP).
-
- Applications: Securing your custom applications, code, and configurations to prevent vulnerabilities.
-
- Operating Systems: Patching, hardening, and configuring the operating systems of your virtual machines.
-
- Network Configurations: Correctly setting up virtual private clouds (VPCs), subnets, security groups, and network access control lists (NACLs) to control traffic flow.
-
- Identity and Access Management (IAM): Managing user identities, roles, and permissions to enforce the principle of least privilege.
-
- Endpoint Security: Protecting virtual servers, containers, and serverless functions with security tools.
As the diagram illustrates, while the cloud provider gives you the secure foundation, you are the one who must build securely on it. Your security posture in the cloud depends entirely on how well you implement these controls for your workloads and data.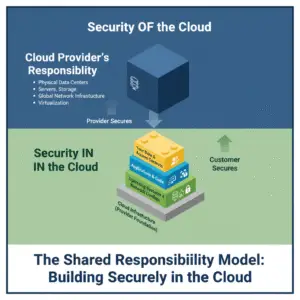
Case Study: Securing a Complex Hybrid Cloud Environment
One of the biggest real-world challenges in cloud security today is managing a hybrid cloud environment—a combination of on-premise infrastructure and public cloud services. Let’s look at a case study of a legacy financial institution’s “Project Nexus” to understand these challenges.
The Scenario: GlobalInvest, a traditional bank, decided to modernize by moving its customer-facing applications and analytics to AWS while keeping its core banking systems and sensitive data on-premise due to strict regulatory requirements.
The Concerns:
-
- Interconnectivity: Securely linking on-premise systems (legacy mainframes, Oracle databases) with the AWS VPCs required careful configuration of VPNs and private connections.
-
- Identity Sprawl: Users needed seamless access to both on-premise applications (via Active Directory) and AWS resources. This created a massive challenge in managing identities and ensuring consistent “least privilege” policies across both environments.
-
- Data Flow: Securely transferring masked customer data from on-premise to AWS for analytics required end-to-end encryption and a robust data governance strategy.
-
- Visibility: The security team lacked a single, unified view of threats and events across both their on-premise security information and event management (SIEM) and AWS-native tools like CloudTrail and GuardDuty.
The Solution: GlobalInvest tackled these challenges by meticulously applying the Shared Responsibility Model and integrating security into every step.
-
- Unified IAM: They federated AWS IAM with their on-premise Active Directory, allowing a single identity to control access to both environments and enforcing multi-factor authentication (MFA) everywhere.
-
- Infrastructure as Code (IaC): They used tools like CloudFormation and Terraform to automate the deployment of their AWS infrastructure and security controls. This ensured consistency and eliminated human error from manual configurations.
-
- Continuous Monitoring: They used AWS Config to continuously monitor for deviations from their security baselines and aggregate all logs and security events into a centralized SIEM for a complete picture.
-
- Data Protection: They mandated encryption for all data at rest and in transit and used native cloud tools to discover and protect sensitive data.
By understanding that they were responsible for securing their workloads in the cloud, GlobalInvest successfully modernized their infrastructure without compromising their security or compliance. The key was a comprehensive approach that bridged the on-premise and cloud divide with a clear strategy and the right tools.
This case study demonstrates that security isn’t just a technical problem; it’s a strategic one. It requires a deep understanding of your responsibilities, a focus on automation, and a commitment to continuous monitoring to protect your digital assets in a complex, multi-faceted environment.


