-
Status:
Completed
-
Client:
Charles Zakrin
-
Location:
Remote
I successfully planned, deployed, and secured a web application on Amazon Web Services (AWS) using a layered security approach. This project demonstrated my ability to implement key cloud security controls, including a Web Application Firewall (WAF), Security Groups, and SSL/TLS encryption, to protect against common web threats.
1. Web Application Deployment
First, I provisioned a basic web application on an EC2 instance within a secure Virtual Private Cloud (VPC). The application was a simple, static site, serving as a foundation for implementing security measures. I configured the necessary networking, including a public subnet for the application and a private subnet for the database (though a database was not part of this specific security scope).
2. Implementing Network and Transport Layer Security
To control traffic at the network level, I created and configured a Security Group for the EC2 instance. This virtual firewall was initially set to deny all inbound traffic. I then created specific inbound rules to allow only HTTP and HTTPS traffic from a trusted source: the Application Load Balancer (ALB). This ensured that no one could directly access the server from the public internet, forcing all traffic to pass through the ALB.
Next, I deployed an Application Load Balancer in front of the EC2 instance. This was a critical step for both scalability and security. I configured the ALB to terminate all incoming HTTPS traffic, offloading the encryption work from the web server. I provisioned a free SSL/TLS certificate from AWS Certificate Manager (ACM) and attached it to the ALB. This ensured that all data transmitted between users and the load balancer was encrypted, protecting sensitive information in transit.
3. Application Layer Security with a WAF
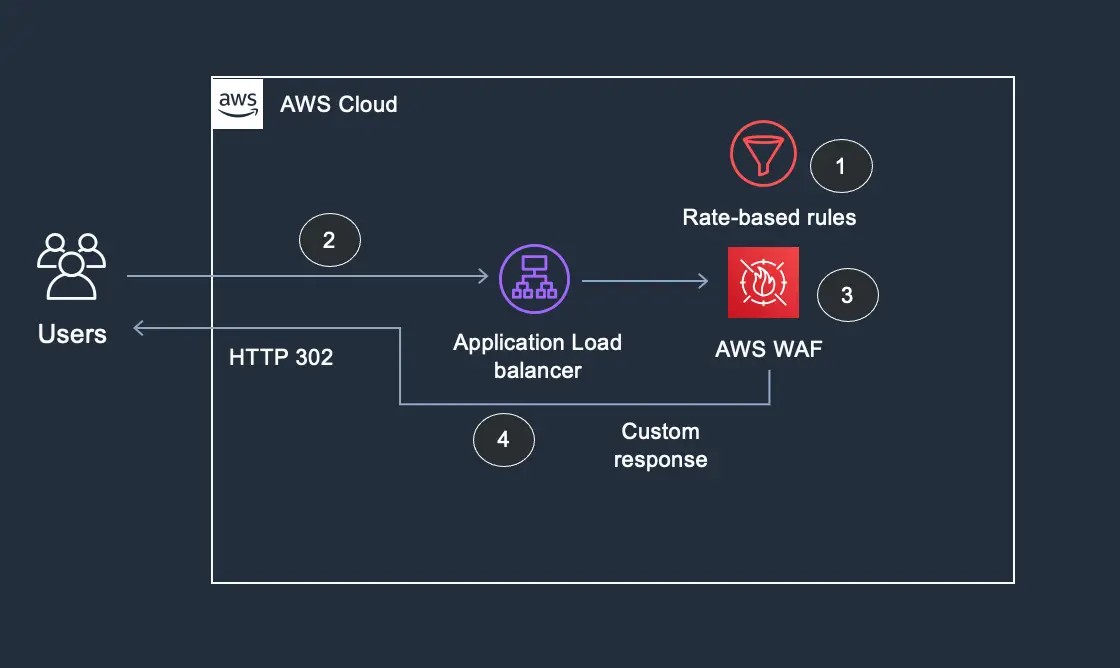
This was the most crucial part of the project. I created an AWS Web Application Firewall (WAF) and associated it with the Application Load Balancer. I then configured a series of WAF rules to protect the application from common web exploits. These included:
-
Managed Rule Sets: I utilized AWS-managed rule groups for SQL injection and cross-site scripting (XSS). These pre-configured rules automatically detect and block known attack patterns, providing a strong baseline defense.
-
Rate-Based Rules: To mitigate Denial of Service (DoS) attacks, I set up a rate-based rule to automatically block any IP address that made an excessive number of requests in a short time frame.
-
Geo-Blocking: I configured a geo-blocking rule to restrict access to the application from specific countries that were not part of the target audience, further reducing the attack surface.
4. Verification and Validation
Finally, I validated the security implementation. I used a web browser to test the SSL/TLS encryption and ensured that the application was only accessible via HTTPS. I also attempted to trigger the WAF rules using simulated SQL injection and XSS payloads. In both cases, the WAF successfully blocked the malicious requests, redirecting me to a "403 Forbidden" page and logging the event in AWS CloudWatch.
This project was a success, resulting in a robust, multi-layered security posture for the web application. I gained hands-on experience in AWS security services, network traffic control, and application-level threat mitigation, proving my ability to build and secure a modern cloud-native application.